DEFY THE CHAOS AND COST OF RANSOMWARE WITH CORE5
1 solution. 5 levels of cyber resilience.
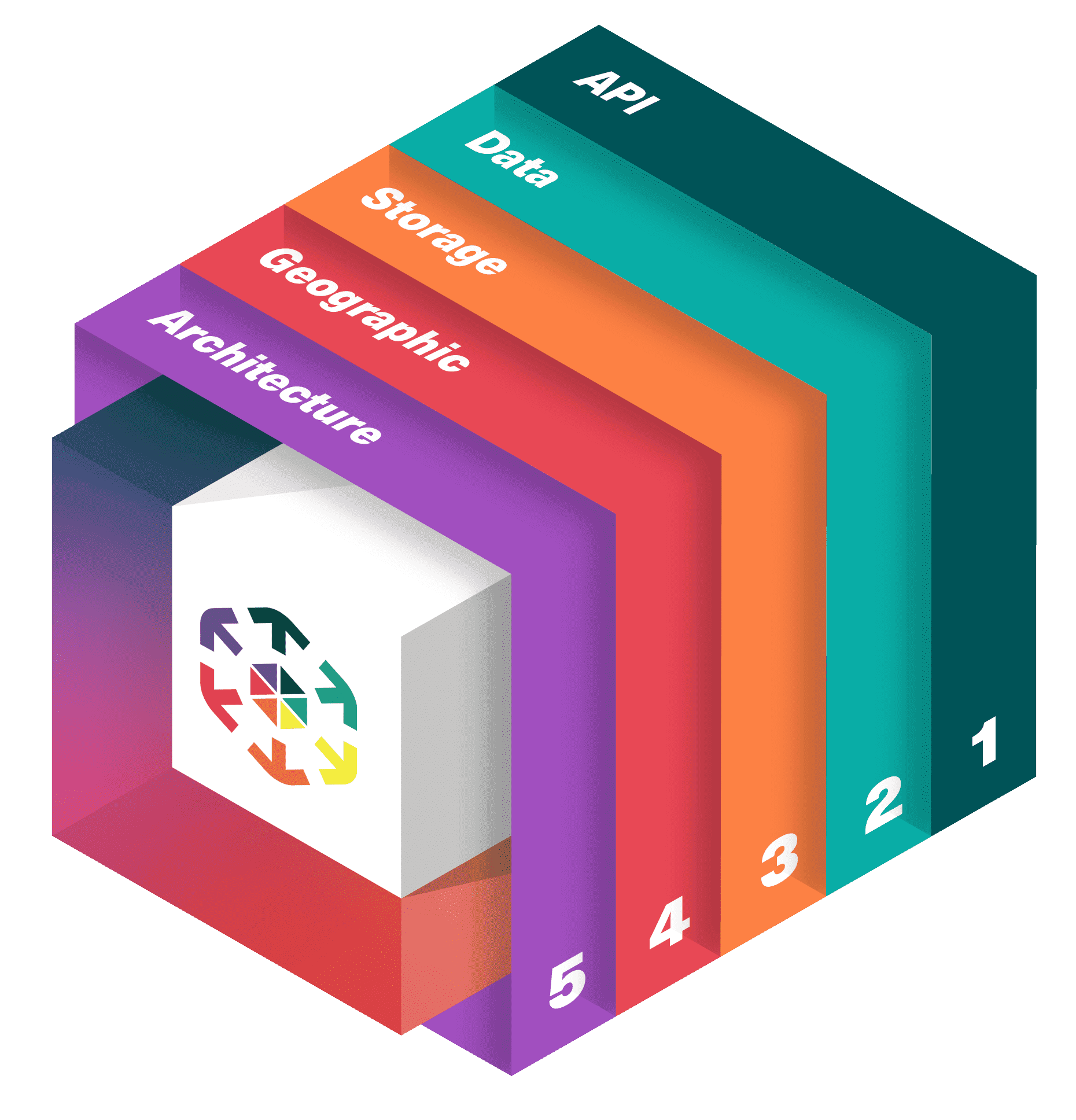
Only Scality storage software enables unbreakable data protection at every level of the system — from API to architecture.
Resilience is a choice. Ransomware is not.
Your current storage system may be immutable, but is it unbreakable?
Immutability has become a cornerstone of cybersecurity. But in the era of AI-powered ransomware, it’s no longer enough.
The vast majority of organizations use immutable storage. Yet the number of victims paying ransoms has doubled.
%
of ransomware attacks actively that target backup storage
%
of IT leaders rely on immutable storage to protect their data
%
increase in victims that paid a ransom over the past year
Your storage infrastructure must go beyond immutability to meet a higher standard of protection.
At Scality, we’ve identified five critical levels of safeguards required to achieve this ambitious level of data protection.
CORE5 is a revolutionary approach that encompasses not only the strongest form of true immutability but also robust, multi-layer protections against data exfiltration attacks, high-level privilege escalation attacks, and other emerging threat vectors.
Make your last line of defense your best.
A new era of ransomware demands a new standard of cyber resilience: CORE5.

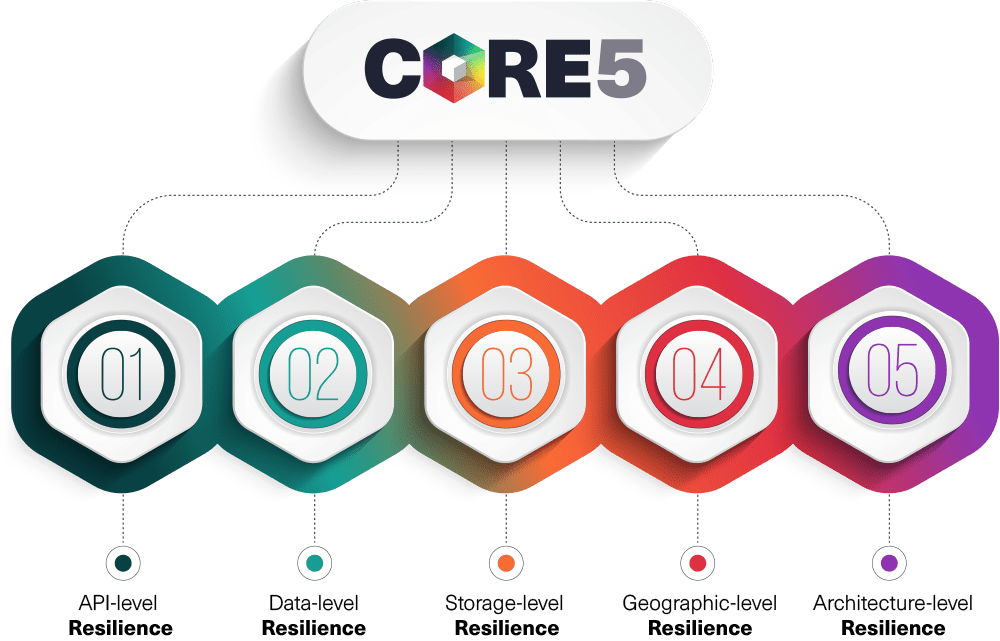
API-level resilience
Immutability implemented at the API level provides a powerful top-line defense against ransomware attacks by ensuring backups are immutable the instant they’re created.
Scality’s support for S3 Object Locking APIs ensures backups are instantaneously immutable. This approach also unlocks a degree of flexibility and ultra-fine granular control that is simply not achievable in legacy storage solutions.
To ensure data remains immutable over specific time horizons as required by business rules and regulatory mandates:
- Configurable retention policies allow you to customize the duration that your data remains fully immutable, whether it’s days, years, or indefinitely.
- Compliance mode provides extra fortification as it prevents even the system super admin from changing immutability configurations.
This degree of customization is advantageous to all businesses and absolutely essential for industries handling sensitive data, such as healthcare and finance, where compliance with stringent regulations is paramount.



Data-level resilience
Multiple layers of data-level security measures are employed to prevent attackers from accessing and exfiltrating stored data.
To keep unwanted eyes off of your most sensitive data, Scality relies on a comprehensive suite of data-level safeguards:
- AWS-compatible authentication and AWS-style IAM features provide ultrafine-grained access control, allowing organizations to define and enforce policies governing user access to data resources. This ensures that only authorized users with the appropriate permissions can access sensitive data, reducing the risk of data exfiltration by unauthorized actors.
- Zero-trust architecture (ZTA) limits malicious access by enforcing a “never trust, always verify” approach to user authentication — users and devices are not trusted by default, even if they are connected to a permissioned network or previously verified.
- Secure HTTPS/TLS termination of S3 endpoints and firewall rules prevents wire-level interception and snooping, ensuring the confidentiality and integrity of data during transit.
- AES 256-bit data-at-rest encryption ensures that even if unauthorized access occurs, the data remains incomprehensible and unusable to the attacker without the appropriate decryption keys.

Storage-level resilience
Advanced encoding techniques are used to prevent destruction or exfiltration of backups by rendering stored data indecipherable to attackers, even those using stolen access privileges to bypass higher-level protections.
To provide forward-looking resilience against threats targeting the storage layer, Scality:
- Implements distributed erasure coding technology, which protects data by fragmenting it into smaller “chunks,” expanding and encoding it with redundant data, then intelligently dispersing those chunks across all drives in the system.
- Goes above and beyond the industry standard by safeguarding the location data for these chunks in a secure hardened repository with its own separate, non-shared authentication and access controls. By denying attackers access to the location of each stored chunk, any data obtained is rendered indecipherable and effectively worthless.
- Uses redundant encoding, allowing for the full reconstruction of any data that is corrupted or lost in an attack, even if multiple drives or an entire server are physically destroyed.



Geographic-level resilience
Simple and affordable multi-site data copies prevent data loss even if an entire datacenter is targeted in an attack.
To mitigate the risks of single-site storage, Scality is designed to make geographic redundancy across multiple sites simple, practical, and affordable. Multi-site replication enables easy data mirroring to remote ARTESCA targets in other data centers, or to cloud storage targets in AWS, Azure, Google, and an increasing number of regional service providers.
Multi-site deployments: For backup applications that manage their own multiple copies and tiers, Scality can be easily deployed and managed remotely.
Additionally, RING can be deployed in a synchronous, multi-site stretched configuration allowing for the temporary or permanent loss of a site due to network and power issues or fire and flood.
Site-specific IAM controls make access to remote sites more difficult for actors with access to the first site, creating multiple “security domains” that an attacker would have to cross in order to access all instances of the data.

Architecture-level resilience
An intrinsically immutable core architecture ensures data is always preserved in its original form once stored, even if an attacker attains the necessary access privileges to bypass API-level immutability.
Scality is designed to provide the absolute strongest ransomware protection possible, right down to the way its core architecture handles data writes to the drive:
- When an application issues a command calling for a data overwrite, Scality’s inherently immutable architecture instead implements that request as a write of a new “object” while retaining a record of the location of the original, untouched data.
- Similarly, requests to delete data instead create a logical marker for the event, leaving the original data intact.
- Multi-factor authentication (MFA) controlled administrator access to system management protects against password attacks and further strengthens security.
- Optional enforcement of mandatory access control restricts root privileges and prevents unauthorized access.

Explore our solutions
Scality RING
Flexible scale-out file and object storage
Scality ARTESCA
Simple, secure S3 object storage
Backup Target
Cyber resiliency, data immutability and efficiency
![]()
Find a reseller
See our channel partners by geolocation
![]()
Request a demo
Get a personalized presentation
![]()
Contact us
Reach out to our dedicated team
